Predictive Maintenance in Industrial Motors
In industrial settings, predictive maintenance is essential to keep machines running smoothly and prevent costly failures. Electrical signature analysis (ESA) is a critical technology in this field, enabling more accurate fault detection in even hard-to-reach electric...
Digital Transformation for Power Plant
Picture by Timothy Cheng Fun, GE Reports. Power system equipment condition monitoring is a must if you wish to ensure the efficiency and reliability of electricity supply. This is typically achieved with equipment maintenance or replacement based on typical service...

Preventing disaster at Power Plant
KievPost FoxNews Chernobyl accident A power plant must be monitored to ensure that it doesn’t fail, which could be a real disaster. That’s why you need an effective monitoring solution to prevent such a scenario. An integrated power plant operation monitoring (PPOM)...
How Artificial Intelligence Is Changing The Retail Landscape
Artificial intelligence is changing retail and businesses that don’t realise this and embrace AI are likely to be left behind. Just look at the numbers - the retail part of the artificial intelligence industry is currently thought to be worth around $26 million....
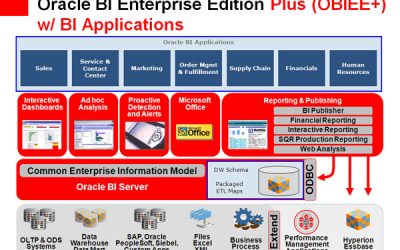
Oracle Looks at BI Trends
Mobile is taking over the Business Intelligence (BI) world. So is the cloud. And Big Data, especially "unstructured" Big Data, is just beginning to revolutionize the ways that enterprises conduct their strategic planning. Those are a few headline results from a new...
The Breaches We Don’t Know About
Stories of major data breaches continue to roll in. One victim announced during the spring was hard drive maker LaCie (now owned by Seagate). In March the firm confirmed a security blog's report that its customer data was exposed to hackers for nearly a year. For...
Security Protection or Morality Police?
Businesses have a right to pick and choose the customers they do business with, so long as they do not violate anti-discrimination laws. And decisions by a particular firm not to cater to specific customers do not keep those customers from doing business elsewhere....
Oracle Looks at EPM Trends
No branch of business operations has been more thoroughly transformed by the computer age than finance, the original "data-driven" business discipline. Successive technology revolutions have given rise to Enterprise Performance Management (EPM) solutions that seek to...
Ignore Bad Data… Sort Of
In George Orwell's classic Animal Farm there is a well-known quote that sums up the issues tackled in the book: "All animals are equal, but some animals are more equal than others". In terms of data, this is a truism: all data is equal, but some data is more equal...
Data May Not Lie – But Liars Can
Figures don't lie, the old saying, but liars can figure. Put another way, even accurate and honest-in-itself data can be presented in misleading ways to support a less-than-honest result. To protect against data-rich lies, we must learn to understand the limitations...
Peeling the Onion of Ransomware
Ransomware attacks on computers are increasing, and they can have devastating consequences. Just look at the heart-breaking story of 17-year-old Joseph Edwards, an autistic college student who killed himself after being on the receiving end of a ransomware email...
Data Governance for Big Data
How many times have you read an article about data quality that uses the phrase "garbage in, garbage out"? It is almost a cliché, but when it comes to big data, there is no other phrase that better sums up the challenges faced by organizations that want to use data...