Where Are People Going With Machine Learning In 2017
Machine learning is an industry in flux. It is not a new industry, but new players are taking the field hoping to make a big impact, sometimes without anything tangible to base that hope on. Many will fail but the result is likely to be a more coherent approach to...
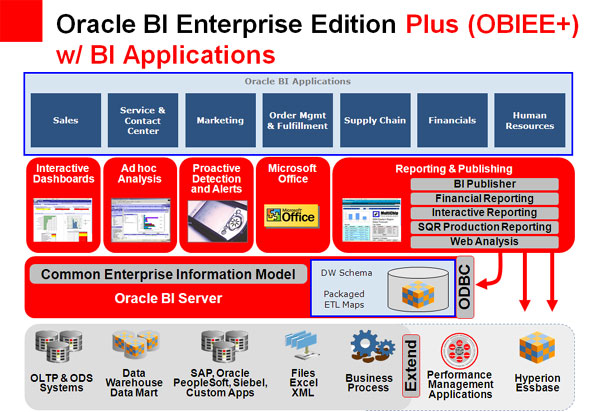
Oracle Looks at EPM Trends
No branch of business operations has been more thoroughly transformed by the computer age than finance, the original "data-driven" business discipline. Successive technology revolutions have given rise to Enterprise Performance Management (EPM) solutions that seek to...

Ignore Bad Data… Sort Of
In George Orwell's classic Animal Farm there is a well-known quote that sums up the issues tackled in the book: "All animals are equal, but some animals are more equal than others". In terms of data, this is a truism: all data is equal, but some data is more equal...
Data Masking
In the modern world of financial services, the protection of your customer's data is critical. Not only critical for your company's reputation but to avoid a whole host of legal and financial obligations should a data breach ever happen. Encryption is one way of...
Protecting Your Mobile Data
According to some studies, over two-thirds of lost smart phones contain sensitive or confidential business information. This can lead to, sometimes serious, breaches of data and confidentiality. With the increasing use of mobile hardware in businesses – whether this...
Is RBAC Dead
For many years one of the easiest ways to control access to data has been through the use of roles. Each user in an organization was traditionally assigned a 'role' by IT security and this role determined the amount of information and level of access granted to the...
Balance Between Top Security And User Access
If anything, recent attacks have shown that there is no single solution to the complex challenge of being protected against insider threats within an enterprise. However, one major defense against such issues is putting in place prudent policies, with strict limits,...
Outdated Software And Its Dangers
Antique, vintage, throwback. These words are often used in today's world to refer to objects that are cool, steady or unique. However, when it comes to software these are the last things you want. This blatant security risk may seem obvious, and no one likes to be...
Managing Your Security Patches
For years, patch management has been a thorn in the side of organizations and continues to be a popular topic of discussion. Management of an organization's security is an increasingly critical aspect of the modern business. Technology continues to evolve and...
Motivated Employees Best Defense
Attacks and raids on private company data are commonplace these days. The easiest way into a company is often for would-be fraudsters to find a disgruntled employee who can leak data. Indeed, this has been the case with several high profile data leaks in the past....
Combating Threats Using Data Analytics
Stories in the media regarding the latest disturbing news about advanced persistent threats (APTs) are now a common sight, affecting well-known institutions, companies and government agencies. The frequency of these threats highlights that even the best IT network...
Is Big Data End For Traditional SIEM
The use of data to tackle incoming threats is nothing new, and basic intrusion detection systems that monitor suspicious activity within a network have been around for at least three decades. However, during this time data volumes have increased exponentially, and...