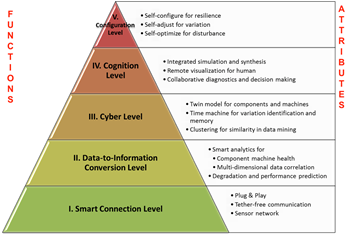
How Machine Learning Makes IoT Relevant
Many of the manufacturers involved in developing IoT technology are still finding a way through the evolving landscape. Most, however, remain focussed on convenience. Convenience products won’t sell in significant quantities, however. Instead IoT devices that are...

The Breaches We Don’t Know About
Stories of major data breaches continue to roll in. One victim announced during the spring was hard drive maker LaCie (now owned by Seagate). In March the firm confirmed a security blog's report that its customer data was exposed to hackers for nearly a year. For...

Security Protection or Morality Police?
Businesses have a right to pick and choose the customers they do business with, so long as they do not violate anti-discrimination laws. And decisions by a particular firm not to cater to specific customers do not keep those customers from doing business elsewhere....
Cloud Computing Is SAAS
Many businesses are increasingly overwhelmed by the complexity of their own data. The solution to this is cloud computing, which eliminates the problem of processing large amount of data. Over the last decade, business intelligence systems have evolved to the point...
Compliance Challenge For Cloud Computing
The single biggest concern for large organizations looking at cloud adoption is still compliance issues, according to a new report by cloud security experts CipherCloud. The survey found that among over 100 respondents, 64% saw compliance as the biggest obstacle to...
Integration Still a Problem Despite Adoption
While uptake has certainly been high—some 93% of businesses now use cloud technology in some form—integration is still an issue. A survey of 930 IT professionals showed that 88% of businesses are using public cloud technologies, while 63% are using private cloud...
Security and Compliance Concerns in the Cloud
A Rackspace study shows that resilience and security will remain top motivations for businesses moving into the cloud throughout 2016. While cost is always a major factor, in a poll of 500 UK IT and business decision makers, resilience, disaster recovery, and security...
Five IoT predictions for 2016
The Internet of Things (IoT) has been discussed for many years, but it still seems to be falling short of its potential. It seems that this year, the promise of software sitting inside a wider variety of devices is set to open up new revenue streams. Device...
How to Fix Mobile BI
With the advent of big data, business intelligence has again been pushed to the forefront of IT's attention. With so many organizations conducting more and more business on the move, mobile devices have been looked to as the answer. That said, the lackluster nature of...
Secure Network Access for Personal Devices
The smartphone phenomenon has reached global proportions, and every day more and more people are expecting to be able to access work materials from their own devices. In fact, almost half of companies now allow employees to use their personal devices to access the...
Location Based Intelligence Software
Using maps to present data is hardly a new phenomenon. Even modern Geographic Information Systems (GIS) have been around for decades, albeit in their own little bubble. These systems, while incredibly useful, required special training and were rarely used outside of...
Data Loss Prevention
In spite of the big headlines about external hacks or insider attacks leading to data loss, it is true that most of the corporate data that gets exposed is through messaging systems. Employees accidentally sending out confidential information through email, instant...