The idea of a layered approach to security is not new, nor is it revolutionary. Just like with old-time castles and modern-day prisons, security on the internet is a multi-layered and multifaceted tool. However, unlike the physical moats, drawbridges, walls and gates – providing an obvious ‘layer’ of security – the reality online is that it is all much more complicated and abstract.
 Using the multi-layered approach of Context Aware Behavioral Analytics, companies like Comcast have cut their security alerts from more than 100,000 an hour to around 100 alerts an hour. This prevents the security team from being flooded with ‘meaningless alerts’ because the amount they are receiving is more than they can handle.
Using the multi-layered approach of Context Aware Behavioral Analytics, companies like Comcast have cut their security alerts from more than 100,000 an hour to around 100 alerts an hour. This prevents the security team from being flooded with ‘meaningless alerts’ because the amount they are receiving is more than they can handle.
There are seven ‘layers’ to this multi-faceted approach to security, writes Brian Donohue for Threatpost.com, describing the use of context aware behavioral analytics for data security.
For a start, there needs to be as much endpoint-focused protection as possible. This should include the obvious features such as malware defense, but also less obvious ones like ‘bio printing’, which analyses how individual users type and use their mouse (e.g., recognizing common or habitual typing errors or mouse movements).
Secondly, network behavior should be examined to spot anomalous activity, which could ultimately suggest the presence of malware or botnet traffic.
The next two layers are increasingly and inextricably linked. The third step watches the behavior of the individual and creates a profile of said behavior. The fourth monitors the ‘baseline’ set by the third and uses that information to flag anomalous activity.
The fifth layer incorporates big-data analytics. Insurance fraud is a prime example, where medical clinics are set up in the middle of nowhere running more brain scans than there are people in the local population or more car crashes than there are cars.
The sixth layer takes in external threat intelligence. This can mean the integration of publicly or commercially available blacklists, network relationships and other information. This can be useful due often-lazy criminals who will use the same accounts and IP blocks across multiple attacks.
The final layer of this approach is about alert-management itself. Security teams “Need to bring all the layers together so that they are [only] receiving relevant alerts.”
Taking such an approach could even have thwarted the now infamous Snowden leaks. Under the seven steps there were several parts of the case that may have been flagged as abnormal. This includes out of hours access across 25 different passwords linked to one IP address and the downloading of 1.7 million files onto a USB stick.
The creation of baseline behavior profiles is important, not only for individuals, but for devices and other entities in order to flag behaviors that may not be abnormal for an individual but rings alarm bells when compared to the entire group. What is certain, is that “Organizations need to align with processes and acquire skills and expertise to make these plans a reality.”
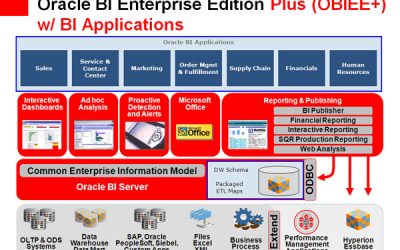
Big Data and related technologies – from data warehousing to analytics and business intelligence (BI) – are transforming the business world. Big Data is not simply big: Gartner defines it as “high-volume, high-velocity and high-variety information assets.” Managing these assets to generate the fourth “V” – value – is a challenge. Many excellent solutions are on the market, but they must be matched to specific needs. At GRT Corporation our focus is on providing value to the business customer.
Oracle Looks at BI Trends
Mobile is taking over the Business Intelligence (BI) world. So is the cloud. And Big Data, especially "unstructured"...